Understanding Mutual TLS (mTLS): The Ultimate Security Mechanism for APIs

In today’s connected world, APIs are the backbone of countless apps, from mobile services to IoT devices. With this growing reliance on APIs, securing their communication is more critical than ever. While traditional TLS (Transport Layer Security) protects data in transit by encrypting it and verifying the server, it falls short when it comes to verifying the client. This is where Mutual TLS (mTLS) shines—it takes security to the next level by ensuring both sides can trust each other.
Let’s dive into what mTLS is, how it works, and why it’s a game-changer for secure communications.
What is Mutual TLS (mTLS)?
Mutual TLS builds on standard TLS by adding client authentication to the mix. Instead of just verifying the server, mTLS ensures the server and the client authenticate each other using digital certificates. This way, both sides can confidently communicate, knowing the other party is legitimate.
In simple terms:
- The client ensures it’s talking to the right server.
- The server ensures it’s talking to an authorized client.
This mutual verification makes it nearly impossible for attackers to sneak in.
How Does mTLS Work?
Here’s the basic flow of how mTLS secures a connection:
- Client Starts the Connection:
- The client sends a
ClientHellomessage to the server, initiating the handshake.
- The client sends a
- Server Shares its Certificate:
- The server sends its TLS certificate, proving its identity.
- Server Requests the Client’s Certificate:
- Unlike regular TLS, the server explicitly asks for the client’s certificate.
- Client Responds with its Certificate:
- The client provides its certificate, proving its identity.
- Mutual Verification:
- Both the server and the client validate each other’s certificates.
- Secure Communication Begins:
- Once validation is successful, the encrypted communication channel is established.
Why Use mTLS?
Here are the main reasons why mTLS is worth considering:
1. Stronger Security
- Both parties must prove their identity, ensuring no unauthorized access.
- Virtually eliminates risks like impersonation or man-in-the-middle (MITM) attacks.
2. Built-In Encryption
- Data exchanged between the client and server is encrypted, protecting it from eavesdropping.
3. No More Passwords
- mTLS relies on certificates, not passwords or tokens, making it more secure and less prone to theft.
4. Industry Compliance
- Many industries, such as finance and healthcare, require secure methods like mTLS to comply with regulations like PCI DSS or HIPAA.
5. Simplified Access Control
- Client certificates can carry metadata (like roles), enabling fine-grained control without extra overhead.
How to Implement mTLS
Step 1: Generate Certificates
You need:
- Server Certificate: To authenticate the server.
- Client Certificate: To authenticate the client.
Here’s an example using OpenSSL:
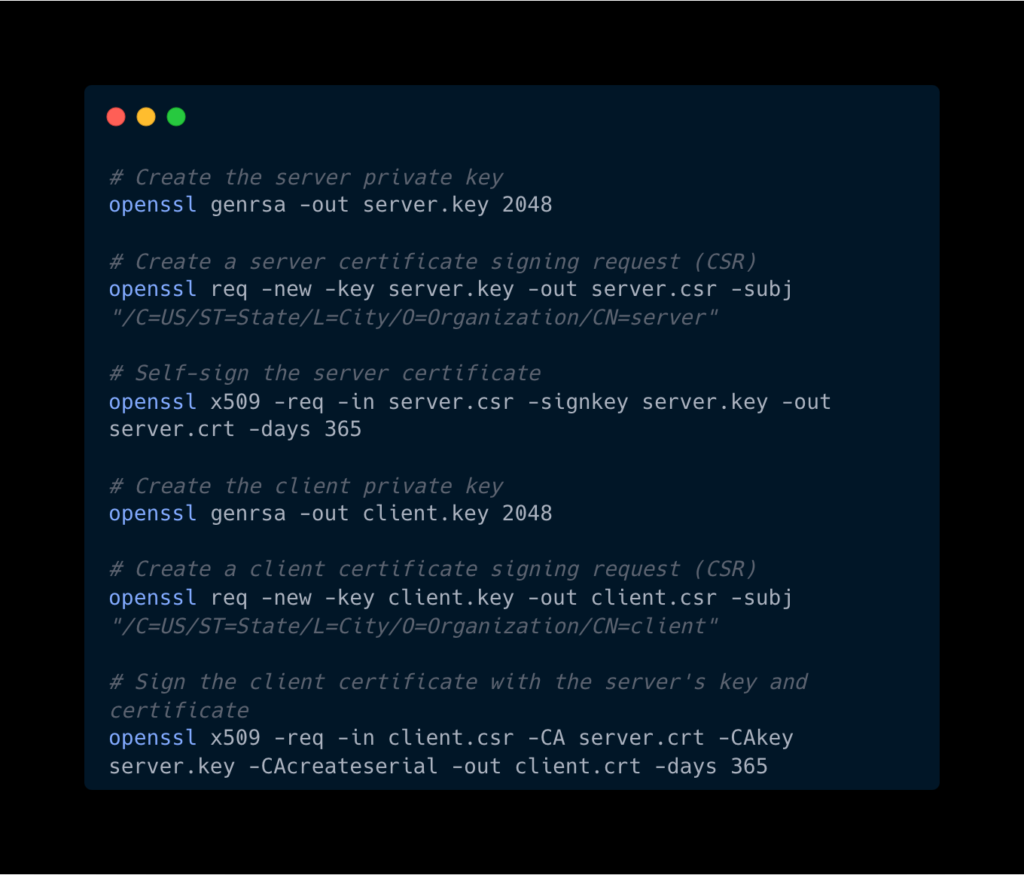
Step 2: Set Up the Server
If you’re using NestJS for the backend, here’s how to configure mTLS:
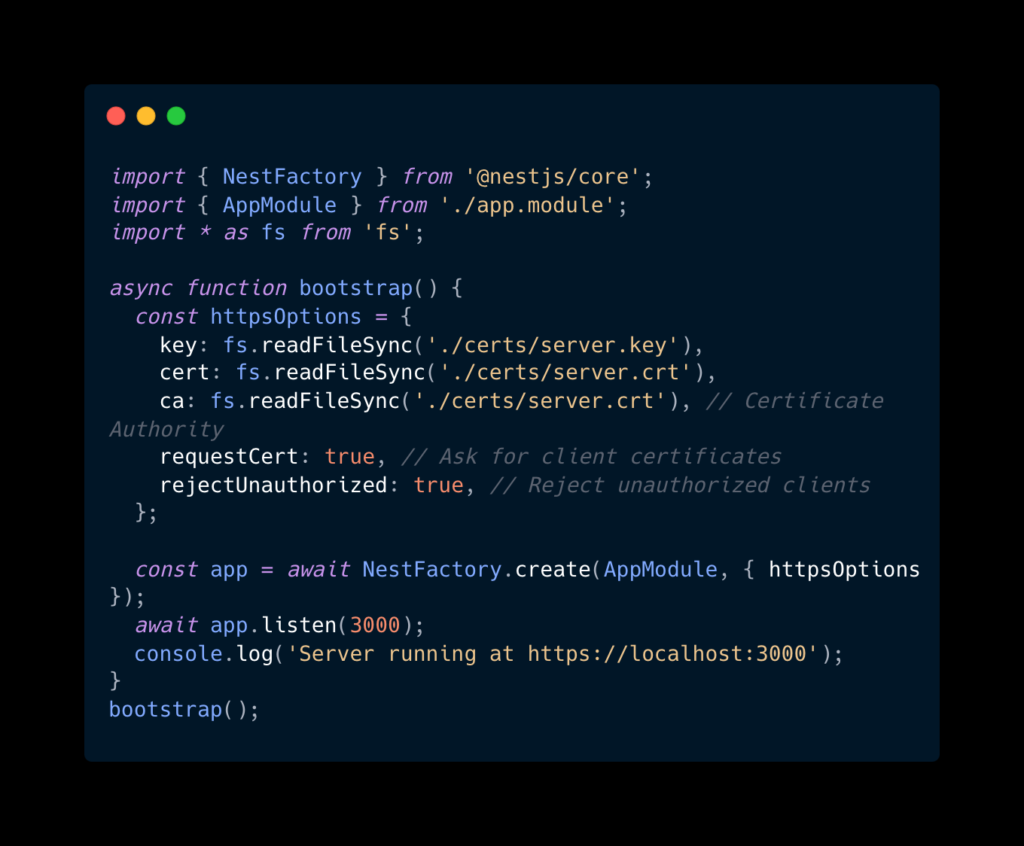
Step 3: Set Up the Client
In Flutter, you can configure the client to use mTLS like this:
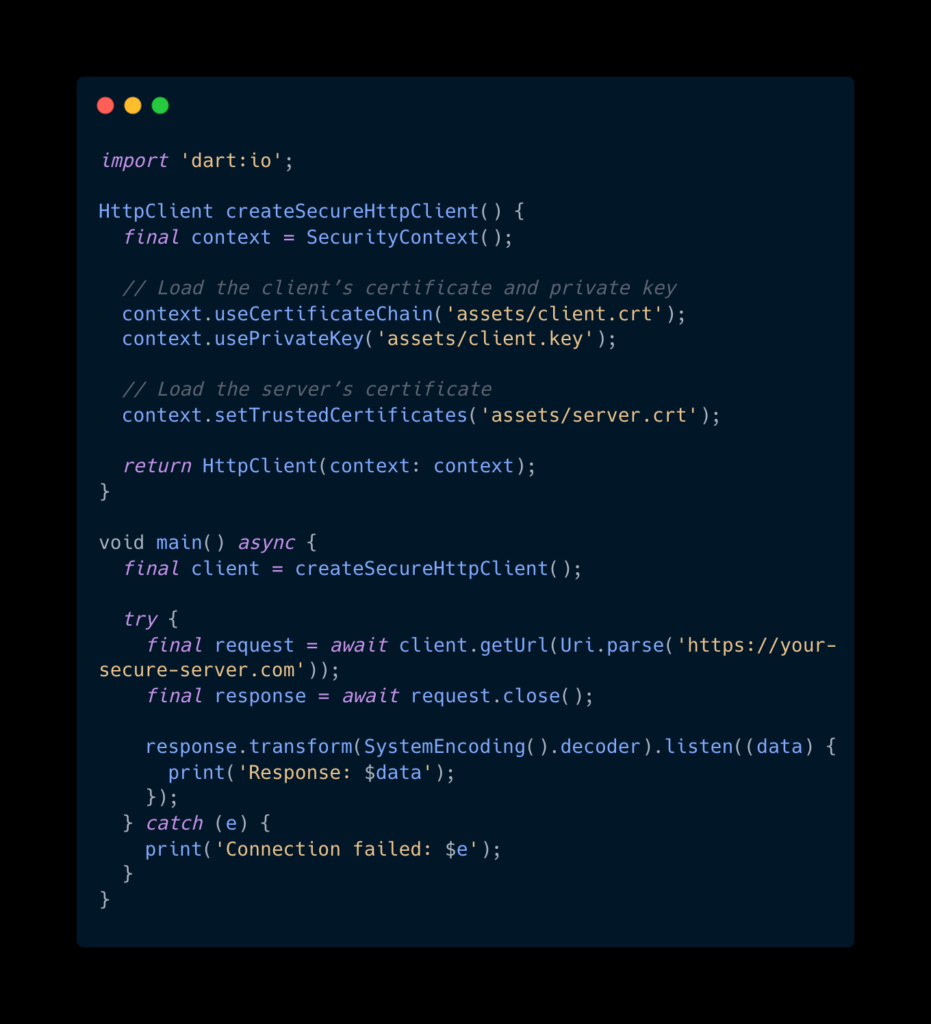
How Does mTLS Compare?
| Feature | API Key/Token | OAuth | mTLS |
|---|---|---|---|
| Authentication | Server-side only | Server-side only | Both client and server |
| Vulnerability to MITM | High | Moderate | None |
| Risk of Credential Theft | High | Medium | None (uses certificates) |
| Encryption Strength | Optional | Optional | Always on |
| Ease of Forgery | Moderate | Moderate | Extremely difficult |
| Best Use Case | Simple apps | Complex apps | High-security systems |
Challenges and Best Practices
While mTLS is incredibly secure, it comes with its own challenges. Here’s how to address them:
1. Certificate Management
- Challenge: Keeping certificates up to date and revoking them if compromised.
- Solution: Use tools like HashiCorp Vault or AWS Certificate Manager to automate this process.
2. Distribution of Client Certificates
- Challenge: Securely delivering certificates to clients.
- Solution: Use secure channels and issue unique certificates for each client.
3. Slight Performance Overhead
- Challenge: The additional certificate validation may slow down initial connections.
- Solution: Cache TLS sessions to improve performance.
When Should You Use mTLS?
Consider mTLS if:
- You’re Dealing with Sensitive Data:
- Banking APIs, healthcare systems, or government data.
- You Need Client Verification:
- Ensuring only specific devices or users can access your system.
- You’re Working in a Regulated Industry:
- Meeting compliance standards like PCI DSS or HIPAA.
Mutual TLS is one of the most secure ways to protect API communication. By requiring both the client and server to authenticate each other, it ensures that only trusted parties can communicate. While it’s more complex to set up than traditional methods, the added security is worth it for high-stakes systems.
If you’re building a secure API, especially for industries like finance, healthcare, or IoT, mTLS should be at the top of your list. Yes, it takes effort, but when security is critical, there’s no better solution.







